Fake Instagram Account Trying to Scam Me for Art
Threat SummaryInstagram Scam #1 — The Modelling JobInstagram Scam #ii — Donations FundInstagram Scam #3 — Cryptocurrency TheftInstagram Scammer #4 — Purchase OffersInstagram Scam #5 — Fake Escort ServicesInstagram Scam #6 — Tinder Cross-Service ScamInstagram Scam #7 — Phishing TacticsInstagram Scam #8 — Instagram Banking company ScamInstagram Scam #9 — Purchase OffersInstagram Scams #10 — Loftier-Profile & Influencers Accounts TheftInstagram Scam #11 — Scam Web Address Profiles Instagram Hacks — Futurity DevelopmentRemove Instagram Scam from Your Computer
 This article has been created in club to assist you by explaining to yous how to remove the Instagram Scam which can exist encountered via electronic mail messages.
This article has been created in club to assist you by explaining to yous how to remove the Instagram Scam which can exist encountered via electronic mail messages.
Our Instagram scam guide reveals all popular social engineering tactics that are used on the popular network. We reveal some of the tiptop trending schemes that can both extract sensitive information from the victims or hijack their money — both real currency and cryptocurrency. Go along reading to learn how to protect yourself.

Threat Summary
| Name | Scam on Instagram |
| Type | Scam |
| Curt Clarification | The Instagram scams aim to access sensitive data, coin or cryptocurrency assets past using complex social technology tricks. |
| Symptoms | Profiles or messages that offer various lucrative proposals to the targets. |
| Distribution Method | Instagram and other related mobile apps . |
| Detection Tool | Come across If Your Arrangement Has Been Affected past malware Download Malware Removal Tool |
| User Experience | Join Our Forum to Discuss Scam on Instagram. |

Instagram Scam #1 — The Modelling Job

A legitimate Instagram profile.
Credits to @stephanytattdevil
Instagram and other social media networks take created an entire new marketing platform that is heavily used by influencers and agencies to promote services and products. Every bit a consequence social applied science scams proliferate across the platform. 1 of the most popular Instagram scams is known equally the "Modelling Job" and information technology is mostly targeted to teenagers and college students. Hijacked profiles of models with many followers or simulated copies usually bulletin the targets and endeavor to manipulate them past offering the job opportunities. The Instagram scammer profiles that are used by the criminals instruct the targets that they need to Skype either with them or their clients. The fake profiles can spam the recipients with many photos and videos every bit "proof" until they concord to do so. Once the Skype call is initiated the targets are manipulated into undressing while at the same time promising them that a lot of money is being sent to them. If the targets refuse to continue with this the scammers will bribery them with threats of exposure.
WARNING!: The fake profiles tin can hands be confused with legitimate models!
This scam is peculiarly dangerous every bit it includes several criminal elements: bribery, sexual piece of work and bullying. And while this is a common scheme in other social network platforms (especially on Facebook) in Instagram this has become one of the most common criminal activities. Partly ane of the reasons why it is and then successful is that the main target group is represented as the majority. The perpetrators of this scam can besides easily scan their targets by assessing their emotional status through their posts and picking out the well-nigh probable victims in an easier style than other platforms.

Instagram Scam #ii — Donations Fund

This scam is taken from a archetype phishing scheme that has its origins back to the first electronic mail scmas. Instagram scammers are sending users messages equally strangers on the social network and ask them for donations. The reasons may be dissimilar:
- Rent & Bills
- Donations for a foundation
- Donations for medical interventions
- Nutrient & Supplies
The scammers volition request the target's bank account in order to "transfer coin". A mutual strategy is to transport fake checks for amounts over 500$ and ask for the the departure to be paid. Nonetheless if this is washed the fake check will bounciness back and the victims will loose the funds and will be fabricated to pay the associated depository financial institution fees. A dangerous fact that concerns this Instagram scam is that in connection with the scam operations a lot of individual data is existence requested.

Instagram Scam #three — Cryptocurrency Theft
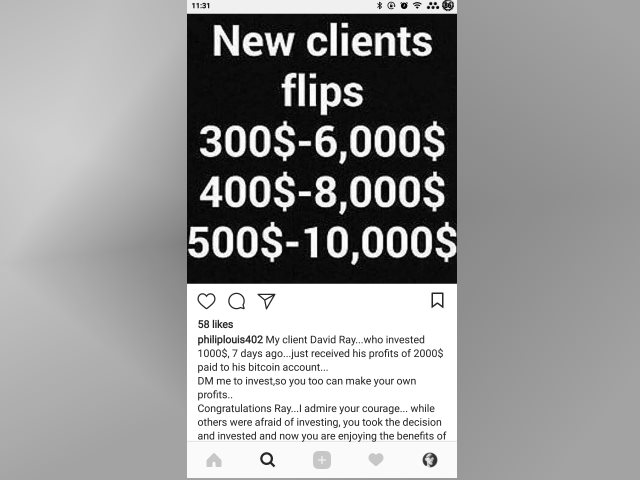
Cryptocurrency related scams are now becoming one of the most numerous blackmail tricks that are used past computer hackers today. The profiles send messages to the predefined targets and advertise the possibility of doubling their digital currency assets in 6 days by offer them "mining services" or "hacks". All the targets need to do is transport the hackers the coins "temporarily" or lend them the public-private key credentials to their wallets. In connection with this the Instagram scammer posts are usually shared on other social networks in order to boost the scam.
Nosotros have reviewed several examples using popular tags and found out that most of the scams are initiated through private messages (DMs). Details are provided to the targets with images and texts that are shown as "proof" of the faux successful enterprise.
This Instagram scam appears to primarily target beginner users that may not know that the promises cannot be completed in this mode. The hackers make use of the fact that a large part of the cryptocurrency communities are not actively moderated. This means that it can also infiltrate chat networks and messaging apps associated with the blockchain projects.

Instagram Scammer #4 — Purchase Offers
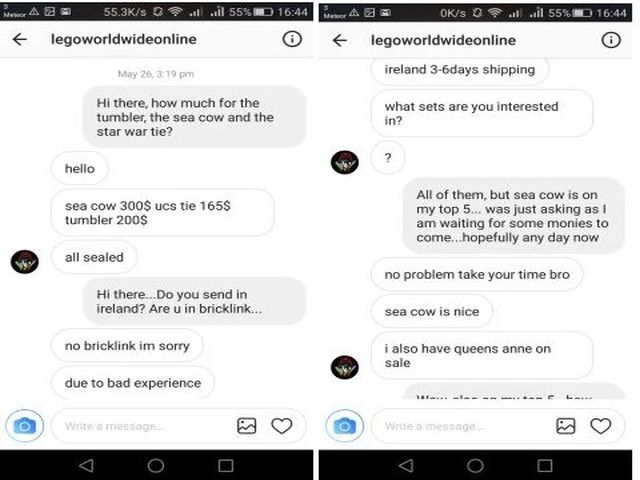
Advertising products for sale on Instagram is one of the preferred marketing tactics. However as much as information technology is used in legitimate sales and promotions the same tactics can be used for scams.
One such instance was described on the Net with an Instagram scammer profile that pretends to exist the official LEGO store. A collector reached out to the criminals with the intention of buying sets from them and gives further details nearly the scam.
The profile has a name that reads just like an official profile of the company and follows accounts that are related both to the operations of LEGO and official fan pages. By interacting with diverse pages it has been able to proceeds a substantial amount of followers. The hackers behind the fake profiles have disabled user comments as a precaution — the victims tin warn other users about the dangers in them.
The conversation with the seller reveals some concerning facts that can indicate that the seller is fake. One of the warning signs is the decline to use emails or any other course of communications besides Instagram. The payment is requested in advance via Western Union, respectively PayPal and other services that provide buyer'south protection are not accepted.

Instagram Scam #5 — Imitation Escort Services

Instagram is a pop platform for meeting people and interacting with people with similar interests. Consequently it has as well been used to postal service offers for escort or adult modeling work. One of the earliest scams that are identified in the platform are the fake escort posts and profiles. They are completely automated and usually have no posts and feature a ane or two line profile clarification.
If they are followed or interacted with in any possible manner they volition send hyperlinks to imitation developed sites that are described as cheap (or free) escort services or dating sites. Instead of posting photos with various tags the bots depend on another strategy — post-obit users in an automated fashion. While this is amid the most common scams on the social networks, users (especially newer to Instagram) can easily fall for this trap.

Instagram Scam #6 — Tinder Cantankerous-Service Scam

A recent scam that has been revealed to be particularly active in the terminal few months. It facilitates the employ of two of the most popular mobile apps — Tinder and Instagram. Fake profiles are created on both platforms used in combination to fool users into falling for their trap. The imitation profile on the dating app is designed to look similar an attractive webcam model. When a target users requests to contact her the hackers share proof that the shared visual content is not fake. This is one of the well-nigh complex scams every bit the criminals will need to provide high quality photos and possibly videos of bonny girls that cannot be found on the Internet along with professional profiles found on developed sites.
The profiles give details that they can come across in exchange for viewing a liveshow and voting for their operation. The targets are sent a link for a trial membership on an adult website. After the paid trial registration is complete the profile cannot be found on the platform.
This scam can be further customized for other like scenarios such as the selling of adult content or personal items. It is possible that the photos and identities of the profiles are stolen equally they appear to be completely legitimate.

Instagram Scam #seven — Phishing Tactics

The estimator criminals can utilise an culling approach that is deemed constructive in many cases. They gear up upward pages that are reminiscent of setting pages, login prompts or other areas used by Instagram users. One of the newer examples of this practise is the spread of such pages on domains that may appear to the end users as used by the service.
The scams are causeless to be operated by experienced users every bit they have taken the web elements and web pattern layout from the service and implemented them in the phishing page. The captured sample pages in the security analysis reveal that these pages in particular contain hybrid content:
- Legitimate Content — The criminals include a help section that may hijack legitimate text and instructions from the official Instagram pages. They are laid out in a similar way to the bodily company page which tin confuse about users into interacting with the malicious elements.
- Phishing Content — In this particular scenario the hackers accept embedded a login prompt into the phishing site. If entered the credentials will be sent automatically to the operators. As a result the criminals can accept over control of the victim accounts.
The assail campaign utilizes an Instagram scam based around the concept of an business relationship migration. The displayed text on the login prompt reads the post-obit message:
Approved Account Participation Course in Instagram
Utilise this form to migrate your account to the operating system and laissez passer the operating system surrender account to the verified account. You lot must login to access the forum.
This gives the users the assumption that the online service can permit them to migrate their accounts during an operating system reinstall. This is conspicuously a scam tactic as the social network is an online service that is not installed as a desktop application.
An additional measures is the inclusion of a Google Maps API which interacts with the stored cookies in the browsers. If the users are logged into their Google account they will see a profile photograph of themselves. This play a joke on is used in order to boost the purposed legitimacy.

Instagram Scam #8 — Instagram Depository financial institution Scam
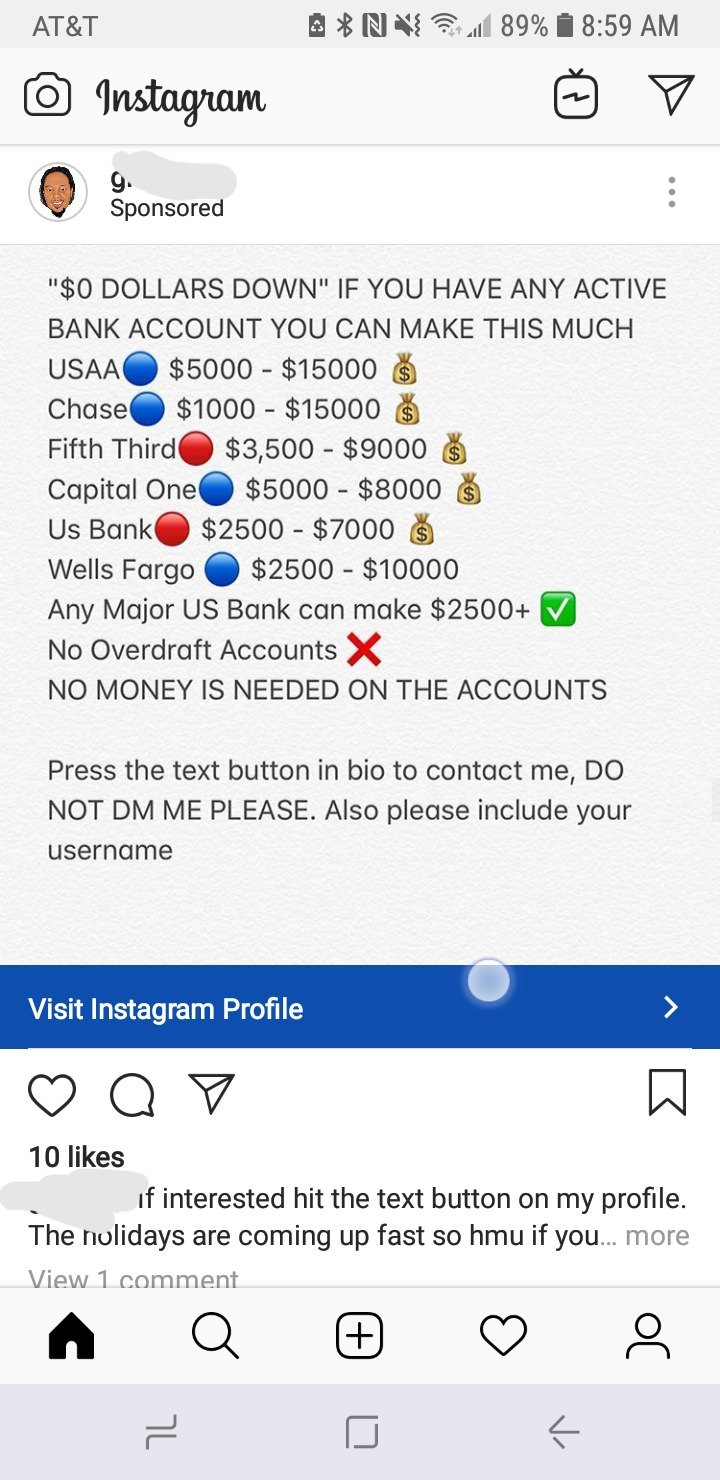
We have received several reports of a pop phishing tactic that makes use of sponsored messages — these are ad-based scams that are straight shown on the timelines when the users open upward the application. The serious issue here is that Instagram have immune the letters to exist distributed without checking them for whatsoever apparent risks.
In that location are two possible hypotheses behind the appearance of the scam messages:
- Deliberate Distribution of Scam Messages — The users that have paid for the ads intentionally target Instagram users with the scam.
- Hacked Accounts — The other hypothesis is that the criminals are spreading the bulletin through compromised accounts of advert agencies and users that accept paid for promoted content.
The Instagram scam bulletin itself volition bear witness a message that appears to come up from an employee or partner of a financial establishment. The users are coerced into contacting them through a text link. It is usually a shortened link that leads to a fake login screen or a scam landing folio. Depending on the exact configuration the attackers volition attempt to dispense the victims into revealing various account credentials or to download virus software.

Instagram Scam #9 — Purchase Offers

Another popular scam is the one associated with habiliment sales. Many merchants have ready their own shops and sell various items — from well-known brands to Chinese knock-offs. At this point the scam tin take place. There are several pop options:
- Faux Make Clothing — Selling apocryphal appurtenances by pretending to exist the official marketplace or an authorized reseller. They may use similar sounding profile names, pattern elements and content.
- Price Scams — The users will be displayed offers of clothing for a price that seems attractive. However the seller has ordered it for a substantially lower toll and as a result the victims will be scammed for paying a high price for a cheap or knock-off detail.
- Scam Items — In this particular case the victims will brand a purchase and will not receive the bought item. Contacting the profile will non assistance as the accounts may be either disabled or hacked in the meantime.

Instagram Scams #ten — Loftier-Profile & Influencers Accounts Theft
With the rise of marketing agencies and influencer accounts several scams surrounding them. Hijacking of such accounts is very unsafe as the criminals can take over control of such accounts and manipulate their letters. This tin can accept a profound impact on both the image of the hacked victim, the brands and services that they are promoting and on the followers. The rising of branded-content scams shows that such activities do happen and that all profiles are potential targets.
The primary idea backside them is to lure the influencers and marketing agencies into thinking that the scammers are legitimate brands. They will create fake ones or impersonate others in sending out phishing links.
All major elements that build up the contour of a "legitimate" Instagram contour are crafted by the hacker operators: the profile name, description and uploaded content. The target users will be contacted through directly messages with offers that simulate the way legitimate profiles exercise.
The sent phishing links will present login pages or surveys that volition asking account credentials to "validate" or correctly open a certain file or process. If such are entered they will exist instantly transferred to the hackers who will steal the accounts.

Instagram Scam #11 — Scam Web Accost Profiles

Some of the hacking groups that are behind the majority of Instagram scams have shifted into launching a slightly different entrada. Their new arroyo is to create profiles that do not utilize usernames or showtime and concluding name combinations. Instead they focus on assigning their names with the addresses of legitimate and well-known services or companies. Past using this approach they add one malicious element that is used in combination with the posts and content.
The detected combinations include the following scenarios:
- All caps full address profiles.
- Lowercase addresses or shortened urls as the profile proper noun.
- Addresses with slight spelling modifications.

Instagram Hacks — Hereafter Development

While Instagram remains one of the most popular platforms for sharing multimedia posts the main reason for choosing it is another. Instagram can connect to many Cyberspace services and software. Combined with the fact that all posts can be tagged with publicly bachelor tags a elementary mail service tin can reach thousands of users in the matter of seconds. The application already comes preinstalled on many mobile devices and this further drives its popularity.
It is very easy for the criminal users to create fake profiles of well-known brands, companies or even people and create SPAM messages that can be artificially boosted using automated means. Criminal collectives (hacker groups) accept started to post scams as shortly equally the service became pop and this has lead to the introduction of such powerful scams that are both damaging to the users and the spoofed targets at the same fourth dimension. As Instagram matures and adds newer functionality so the possibilities of creating newer and more complex scams.

Remove Instagram Scam from Your Computer
In order to brand certain that the Instagram Scam scam is fully gone from your computer, we recommend that you lot follow the removal instructions underneath this article. They have been divided in manual and automatic removal manuals so that they tin help you delete this threat based on your malware removal experience. If manual removal is not exactly something that you feel confident in doing, recommendations are to remove this malware or cheque if it has your infected your computer automatically by downloading and scanning your computer via an advanced anti-malware program. Such software will effectively make certain that your PC is fully secured and you lot passwords and data remain prophylactic in the future.
- Guide 1: How to Remove Scam on Instagram from Windows.
- Guide two: Get rid of Scam on Instagram on Mac OS X.
- Guide 3: Remove Scam on Instagram in Google Chrome.
- Guide 4: Erase Scam on Instagram from Mozilla Firefox.
- Guide 5: Uninstall Scam on Instagram from Microsoft Edge.
- Guide 6: Remove Scam on Instagram from Safari.
- Guide 7: Eliminate Scam on Instagram from Internet Explorer.
- Guide viii: Disable Scam on Instagram Push Notifications in Your Browsers.
Windows Mac OS X Google Chrome Mozilla Firefox Microsoft Edge Safari Internet Explorer Stop Push Pop-ups
How to Remove Scam on Instagram from Windows.
Step 1: Kicking Your PC In Safe Mode to isolate and remove Scam on Instagram
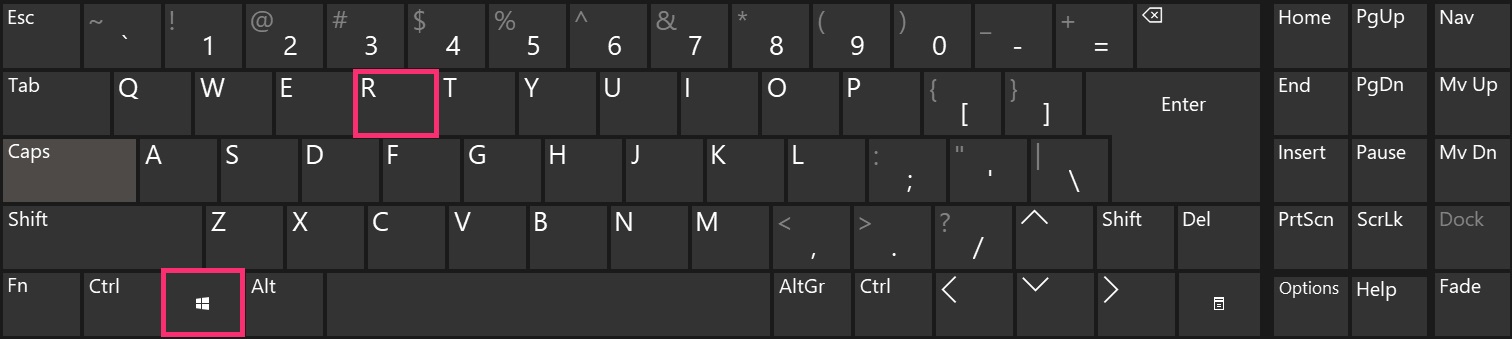
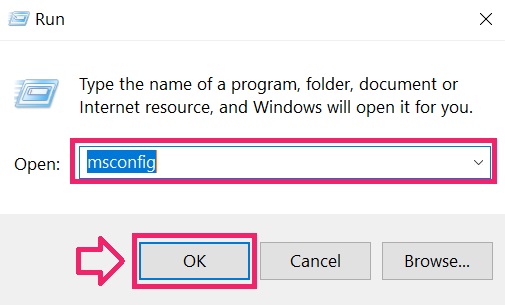

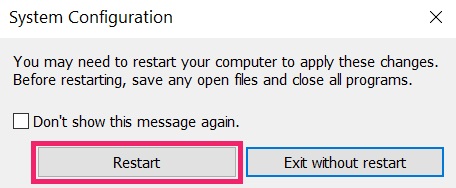

Step 2: Uninstall Scam on Instagram and related software from Windows
Here is a method in few easy steps that should be able to uninstall most programs. No affair if you are using Windows 10, eight, seven, Vista or XP, those steps will get the job done. Dragging the plan or its folder to the recycle bin tin can be a very bad decision. If you do that, bits and pieces of the program are left behind, and that can lead to unstable work of your PC, errors with the file type associations and other unpleasant activities. The proper fashion to get a program off your computer is to Uninstall information technology. To do that:


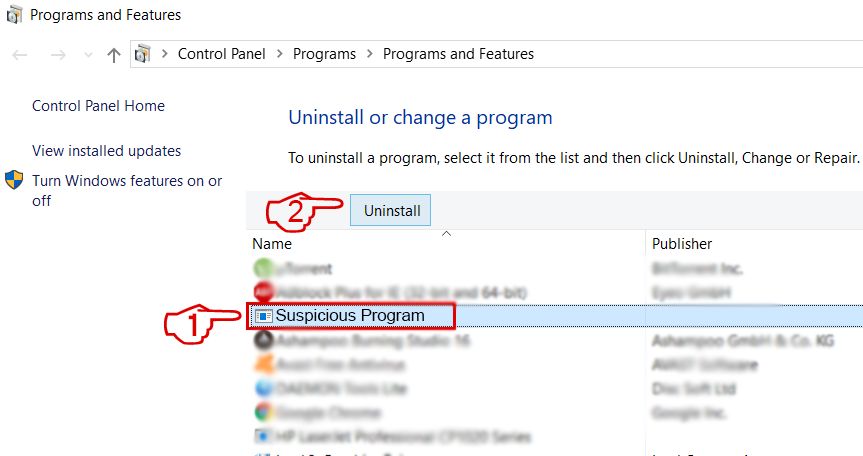 Follow the instructions above and you will successfully uninstall most programs.
Follow the instructions above and you will successfully uninstall most programs.
Step three: Make clean any registries, created by Scam on Instagram on your computer.
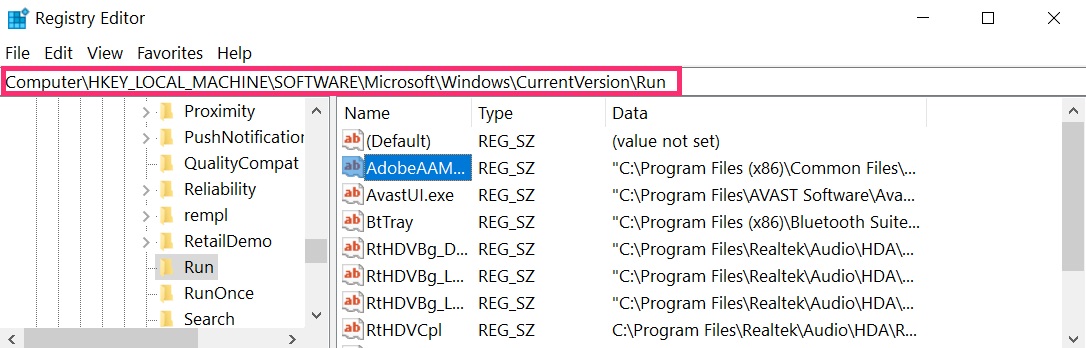
The commonly targeted registries of Windows machines are the following:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
You can access them by opening the Windows registry editor and deleting any values, created past Scam on Instagram there. This can happen past post-obit the steps underneath:
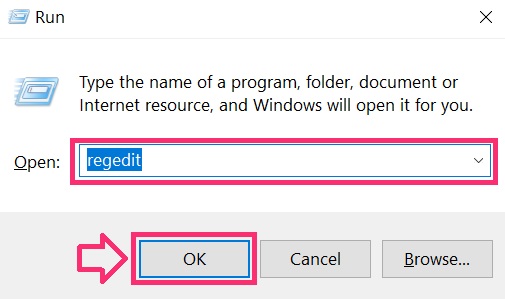
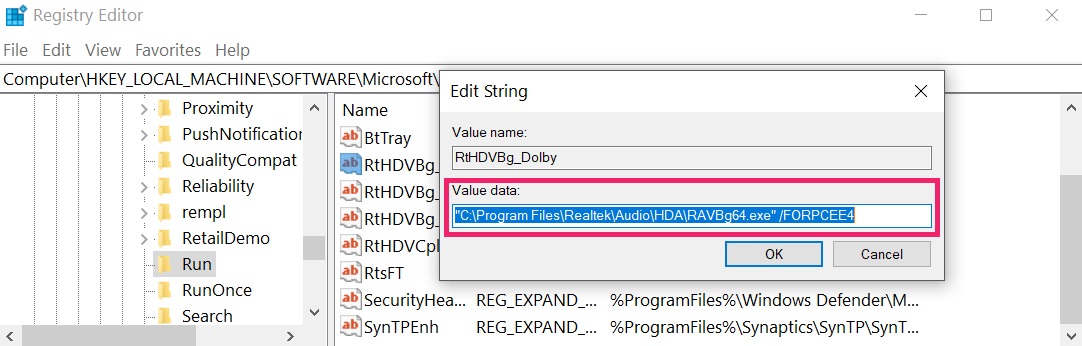 Tip: To notice a virus-created value, you can right-click on it and click "Change" to see which file information technology is set to run. If this is the virus file location, remove the value.
Tip: To notice a virus-created value, you can right-click on it and click "Change" to see which file information technology is set to run. If this is the virus file location, remove the value.
Important!
Before starting "Step 4", please kick back into Normal mode, in case yous are currently in Rubber Fashion.
This volition enable y'all to install and use SpyHunter 5 successfully.
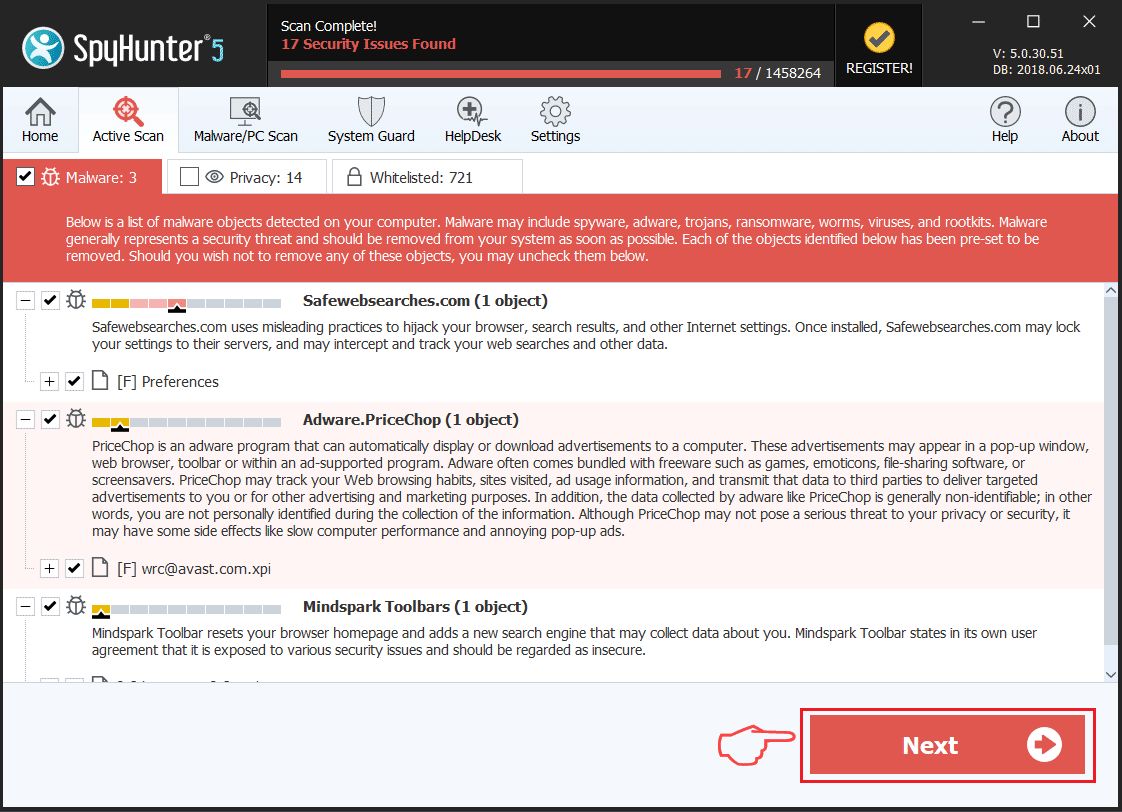
Pace iv: Browse for Scam on Instagram with SpyHunter Anti-Malware Tool


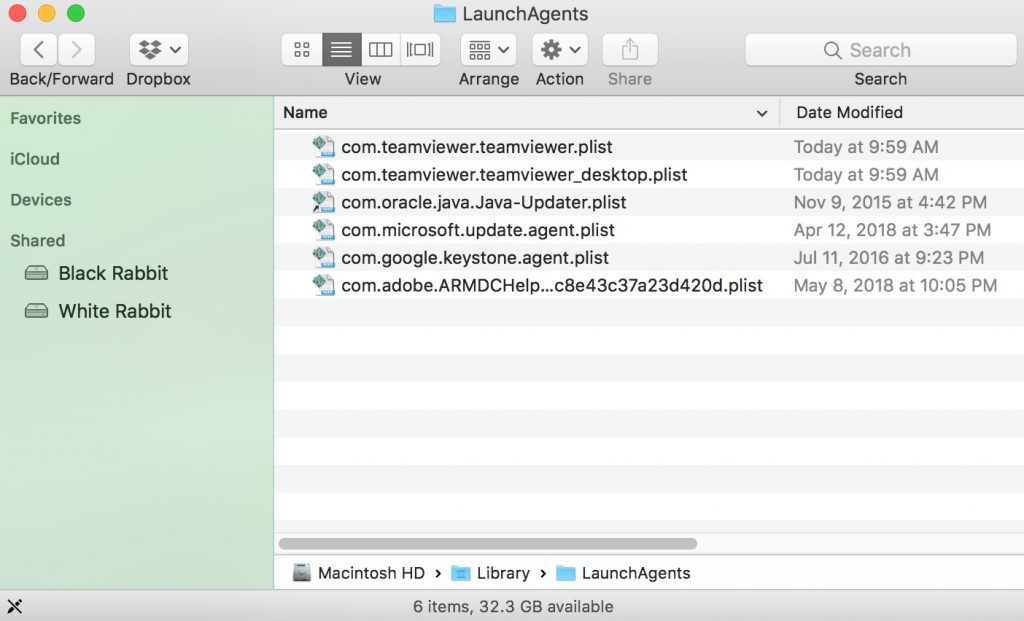
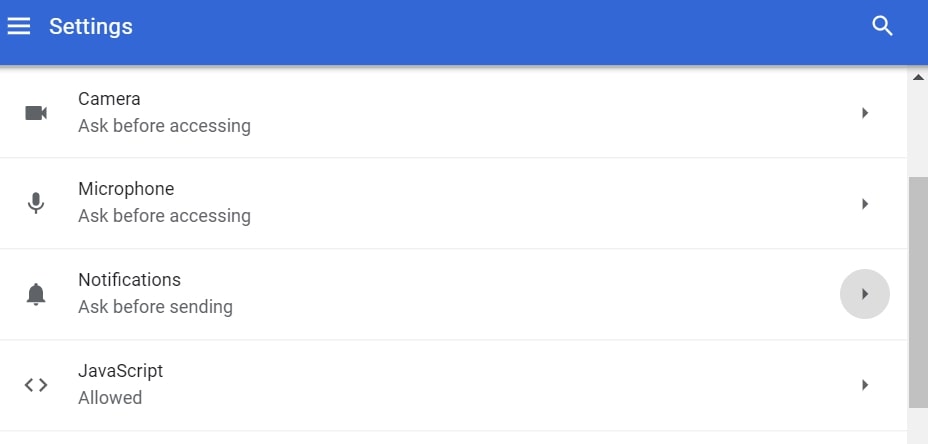
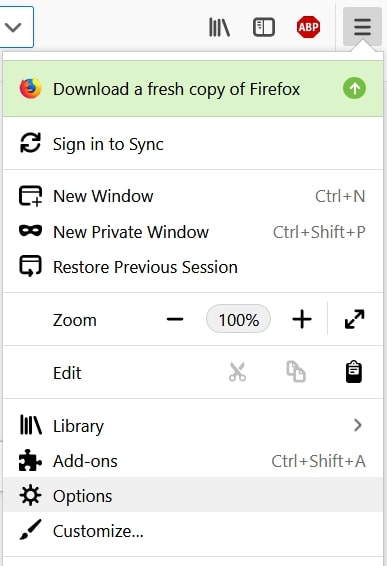
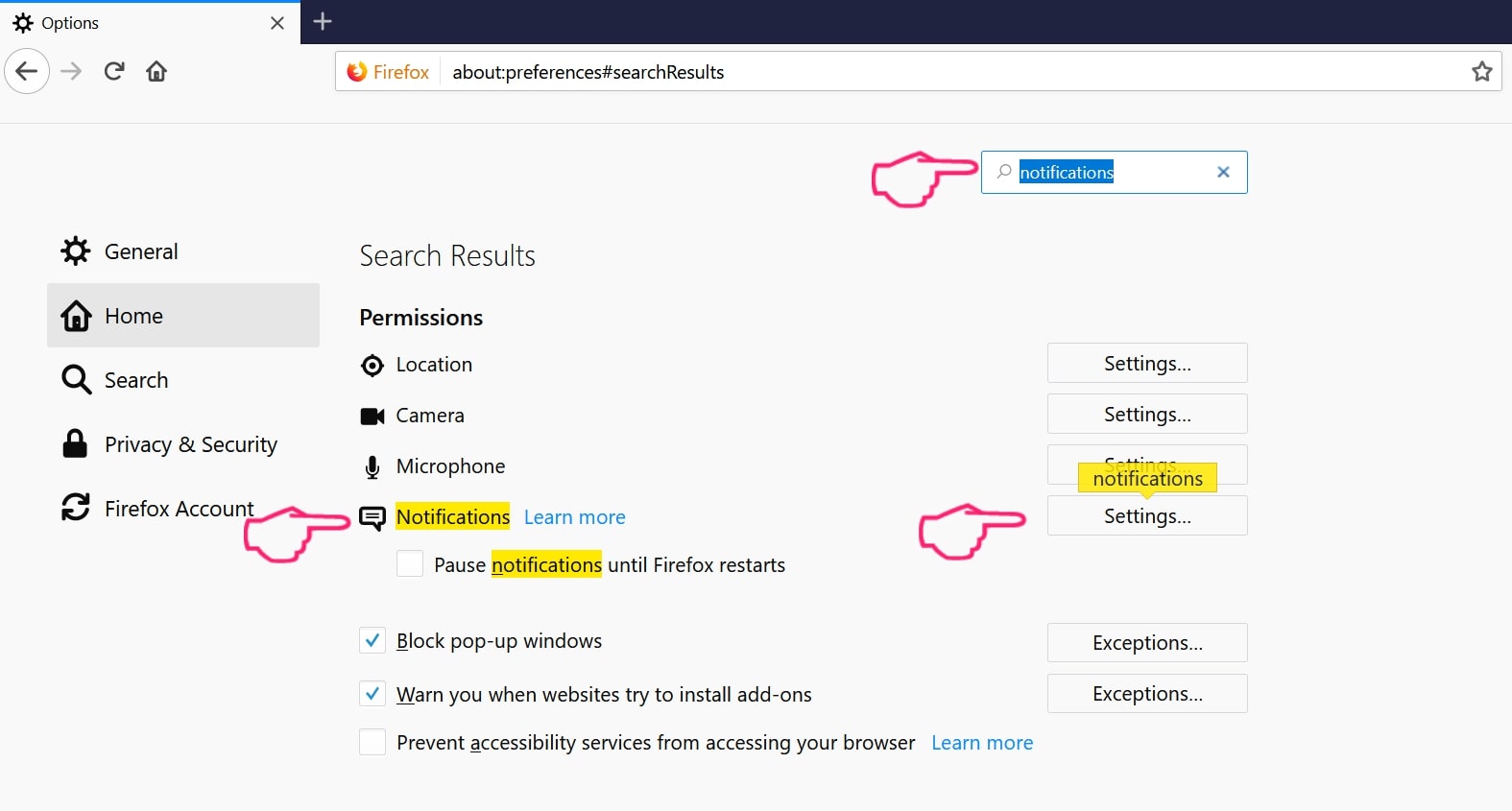
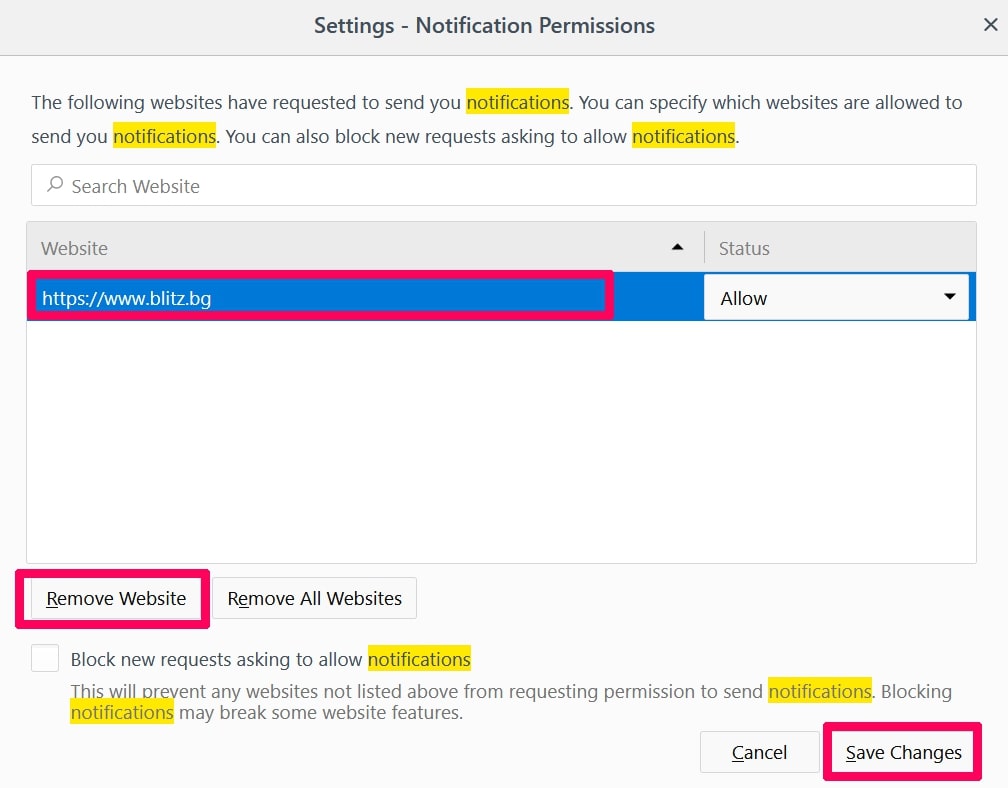
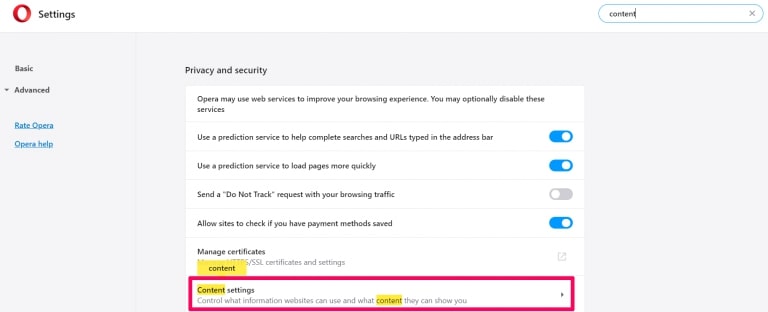
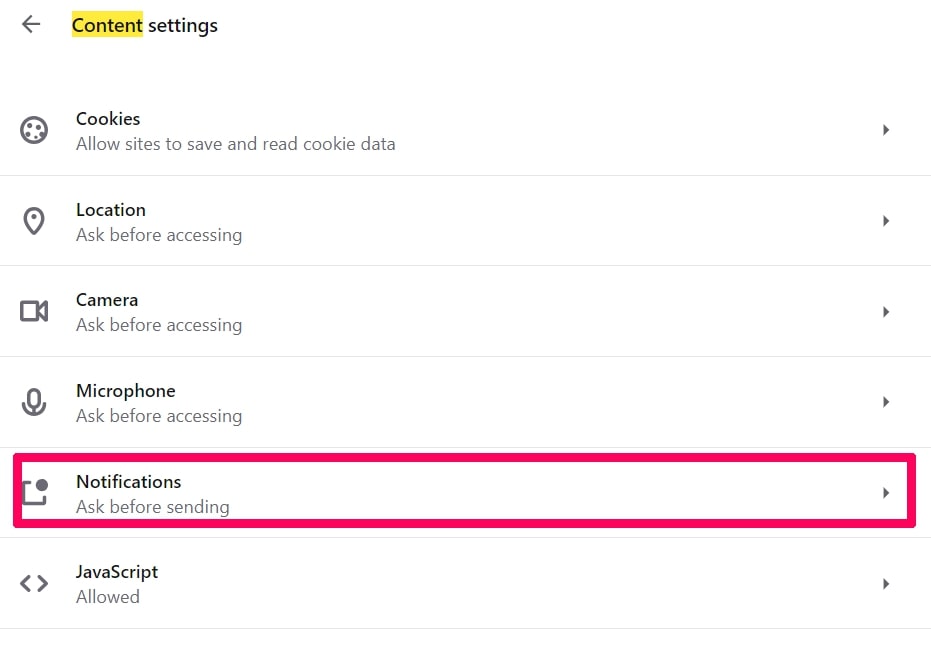
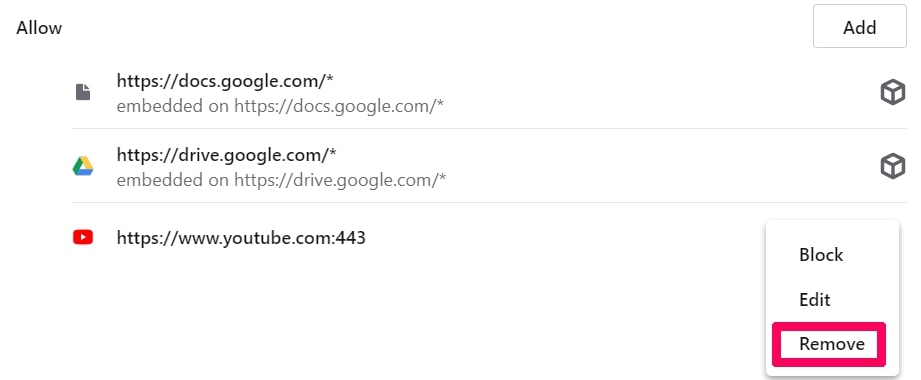
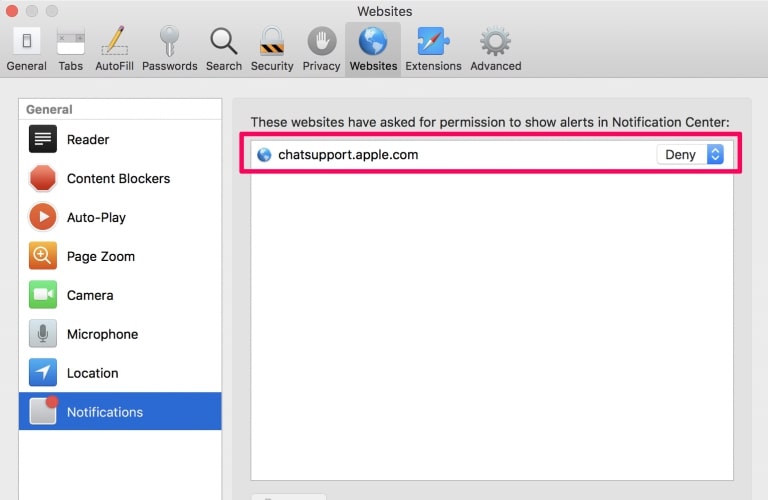
Step 1: Uninstall Scam on Instagram and remove related files and objects In instance you cannot remove Scam on Instagram via Step 1 to a higher place: In case you cannot detect the virus files and objects in your Applications or other places nosotros have shown above, y'all can manually look for them in the Libraries of your Mac. Merely before doing this, delight read the disclaimer below: Disclaimer! If y'all are about to tamper with Library files on Mac, be sure to know the name of the virus file, because if y'all delete the wrong file, it may crusade irreversible damage to your MacOS. Continue on your ain responsibility! You can repeat the same process with the post-obit other Library directories: → ~/Library/LaunchAgents Tip: ~ is there on purpose, because it leads to more LaunchAgents. Step 2: Browse for and remove Scam on Instagram files from your Mac When you are facing problems on your Mac as a outcome of unwanted scripts and programs such as Scam on Instagram, the recommended style of eliminating the threat is by using an anti-malware program. SpyHunter for Mac offers advanced security features forth with other modules that will meliorate your Mac's security and protect it in the hereafter. Download SpyHunter for Mac Stride 1: Start Google Chrome and open the drop carte Pace two: Move the cursor over "Tools" and then from the extended menu cull "Extensions" Step iii: From the opened "Extensions" menu locate the unwanted extension and click on its "Remove" button. Footstep four: After the extension is removed, restart Google Chrome by closing it from the carmine "X" push at the summit right corner and kickoff it once more. Step 1: Commencement Mozilla Firefox. Open the bill of fare window Step 2: Select the "Add-ons" icon from the menu. Step 3: Select the unwanted extension and click "Remove" Step 4: Later on the extension is removed, restart Mozilla Firefox past closing information technology from the ruby-red "10" button at the elevation correct corner and offset information technology again. Step 1: Start Edge browser. Stride 2: Open the drib menu by clicking on the icon at the height correct corner. Step 3: From the drop carte select "Extensions". Step 4: Choose the suspected malicious extension you want to remove and and then click on the gear icon. Step 5: Remove the malicious extension by scrolling down and then clicking on Uninstall. Pace 1: Start the Safari app. Stride ii: After hovering your mouse cursor to the elevation of the screen, click on the Safari text to open up its drop down carte. Stride 3: From the menu, click on "Preferences". Step 4: After that, select the 'Extensions' Tab. Step 5: Click once on the extension y'all want to remove. Stride 6: Click 'Uninstall'. A popular-upward window will appear asking for confirmation to uninstall the extension. Select 'Uninstall' again, and the Scam on Instagram will exist removed. Step 1: Offset Internet Explorer. Footstep 2: Click on the gear icon labeled 'Tools' to open the drop carte du jour and select 'Manage Add-ons' Step iii: In the 'Manage Add together-ons' window. Step iv: Select the extension you want to remove and so click 'Disable'. A popular-upward window will appear to inform you that you are about to disable the selected extension, and some more add-ons might be disabled as well. Leave all the boxes checked, and click 'Disable'. Step 5: Later on the unwanted extension has been removed, restart Internet Explorer past closing it from the red 'X' push located at the top right corner and start it again. Turn Off Button Notifications from Google Chrome To disable any Push Notices from Google Chrome browser, please follow the steps beneath: Step ane: Go to Settings in Chrome. Footstep two: In Settings, select "Advanced Settings": Step 3: Click "Content Settings": Step 4: Open "Notifications": Step 5: Click the three dots and choose Cake, Edit or Remove options: Remove Button Notifications on Firefox Step 1: Go to Firefox Options. Step 2: Go to "Settings", type "notifications" in the search bar and click "Settings": Stride 3: Click "Remove" on any site you wish notifications gone and click "Save Changes" Cease Push Notifications on Opera Step i: In Opera, printing ALT+P to become to Settings Step two: In Setting search, type "Content" to get to Content Settings. Step three: Open Notifications: Pace 4: Exercise the same as yous did with Google Chrome (explained below): Eliminate Push Notifications on Safari Footstep 1: Open Safari Preferences. Stride ii: Choose the domain from where you like button pop-ups gone and change to "Deny" from "Permit".
Windows Mac Bone X Google Chrome Mozilla Firefox Microsoft Edge Safari Cyberspace Explorer Finish Push Pop-ups
Get rid of Scam on Instagram from Mac Os X.
1. Hit the ⇧+⌘+U keys to open Utilities. Some other mode is to click on "Go" and then click "Utilities", like the image below shows: 
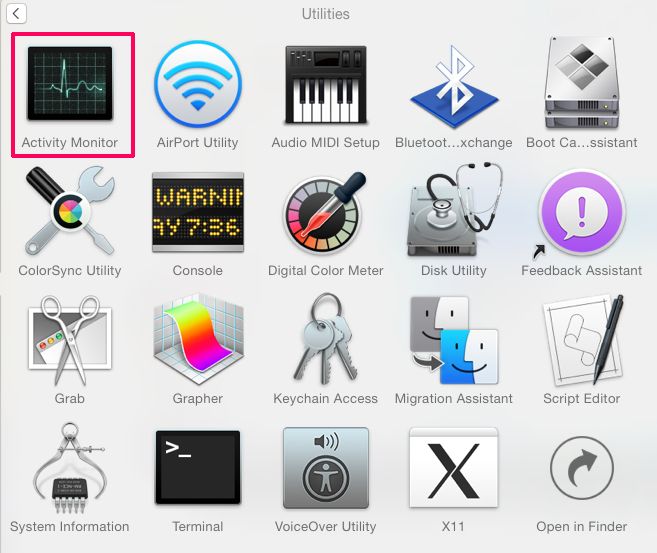

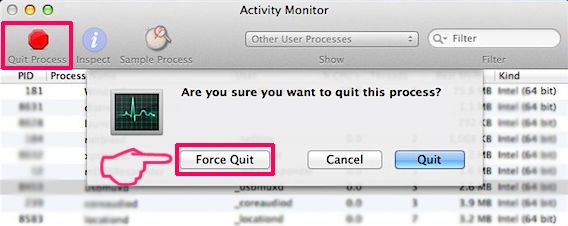
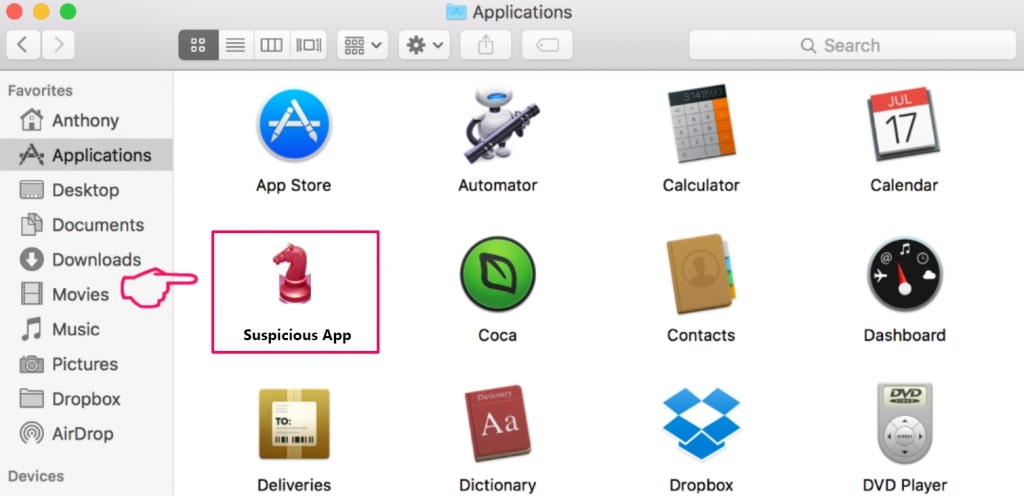
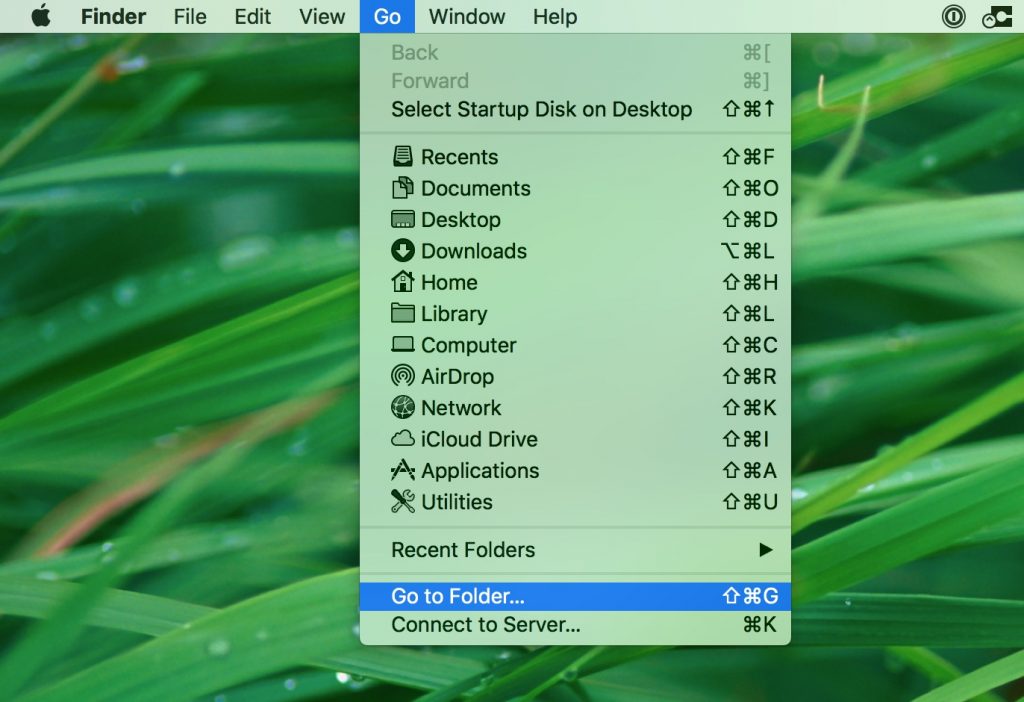
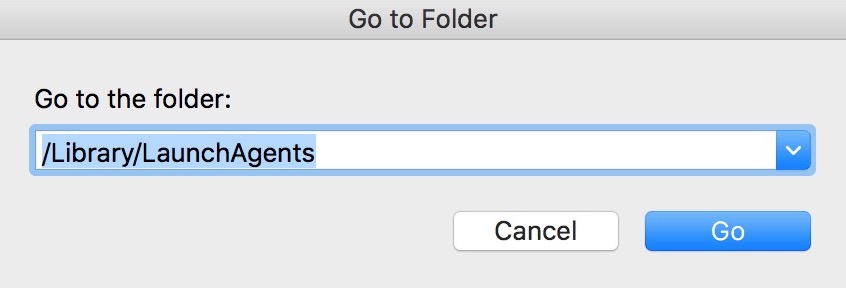
/Library/LaunchDaemons
Windows Mac OS Ten Google Chrome Mozilla Firefox Microsoft Border Safari Net Explorer Stop Push Pop-ups
Remove Scam on Instagram from Google Chrome.



Windows Mac Os X Google Chrome Mozilla Firefox Microsoft Edge Safari Net Explorer Terminate Push Pop-ups
Erase Scam on Instagram from Mozilla Firefox.



Windows Mac Bone 10 Google Chrome Mozilla Firefox Microsoft Edge Safari Internet Explorer End Button Pop-ups
Uninstall Scam on Instagram from Microsoft Edge.




Windows Mac OS X Google Chrome Mozilla Firefox Microsoft Edge Safari Internet Explorer Stop Button Pop-ups
Remove Scam on Instagram from Safari.
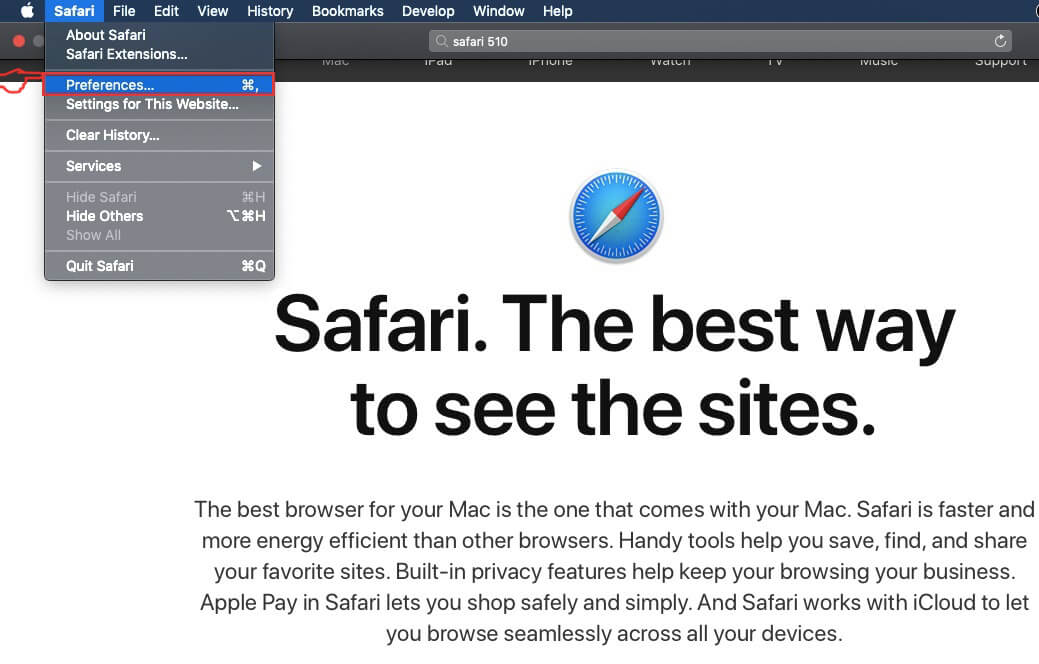
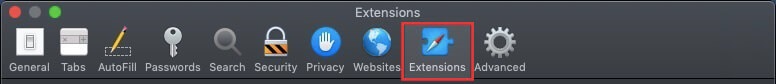
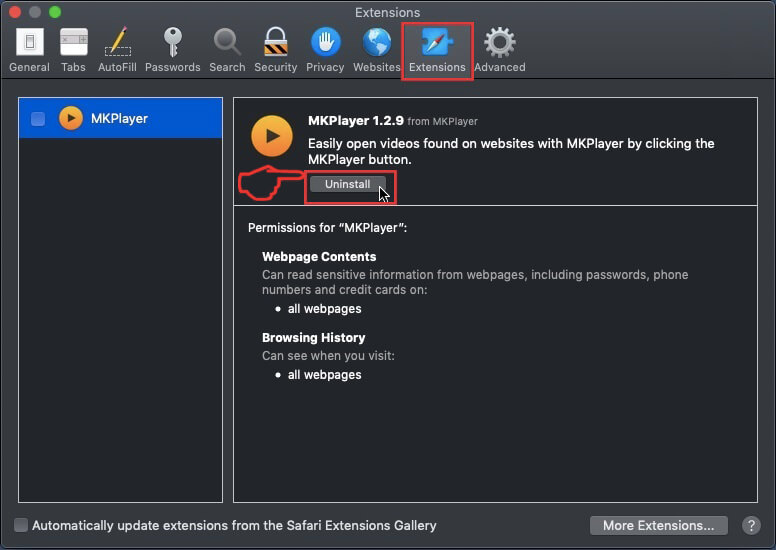
Windows Mac OS 10 Google Chrome Mozilla Firefox Microsoft Border Safari Cyberspace Explorer Stop Push button Pop-ups
Eliminate Scam on Instagram from Internet Explorer.



Remove Push Notifications caused by Scam on Instagram from Your Browsers.


Source: https://sensorstechforum.com/instagram-scam-guide-detect-evade/

0 Response to "Fake Instagram Account Trying to Scam Me for Art"
Post a Comment